Stay informed with the latest information, events, and news. We bring you interesting updates that will keep you connected with our projects and innovations.
Logmanager – security first
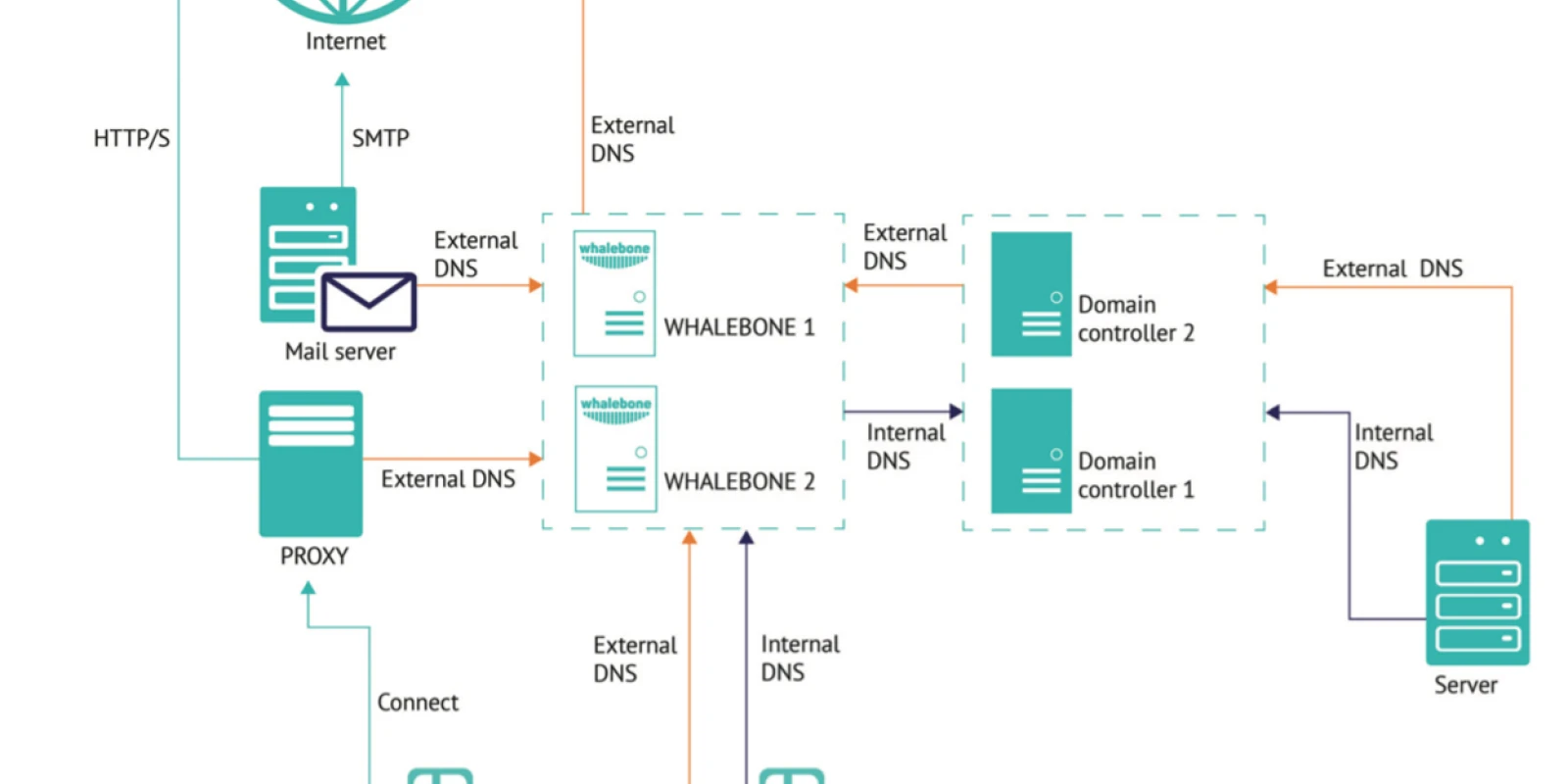
Initial communication between the server and AGENT takes place using TLS 1.2, after establishing the connection everything runs on TLS 1.3. There is also the option to use SSL certificate validation to push security even further.
Security is also enhanced by the AGENT's new ability to collect logs even from non-domain computers. Using Windows registries you can force the AGENT to send logs to any LOGmanager. This option ensures that logs from all supported devices (backup servers, industrial or hospital systems) reach the server.
1200 users in one test campaign
50% gave us their access to email and Office 365
20% opened the attached file
7% extracted the attachment to disk
100% success of the attack
Common targets of attackers using phishing campaigns
Will stop your company
Encrypts data and backups and demands ransom. The company stops, loses 6 months of work and it takes additional months to return to normal.
Will abuse your data
Steals sensitive information and either publishes it or sells it to your competition. The damage can be incalculable.
Will steal your identity
How much can they steal from you before someone notices changes in invoices? After all, they came from the company email.
The changes that the NIS2 directive brings are so fundamental that NÚKIB approached this task by preparing a completely new cybersecurity law and its regulations. This is the first proposal from NÚKIB processed shortly after the official publication of the NIS 2 directive. It can be expected that the regulatory proposals will change, both based on public comments and within the standard legislative process. Given the ever-increasing number of cybersecurity incidents, the rising costs they bring, and the effectiveness of the new NIS2 directive, it pays to deal with cybersecurity immediately.
80% of attacks exploit human errors. Therefore, the number of phishing attacks in the Czech Republic has increased by more than half compared to last year, as reported by NÚKIB.
In preparation for the new cybersecurity law, we recommend that all existing and new obligated entities conduct a comprehensive cybersecurity audit, through which the organization's state will be evaluated from technical, organizational, and legal perspectives, and based on the audit results, targeted solutions will be adopted in accordance with the NIS2 directive.
Data recovery
Microsoft M365 allows quick recovery of recently deleted data. Deleted data can be recovered within 30 days of deletion, but it's important to realize that Microsoft does not perform any backups of your data. Microsoft is not responsible for protecting and storing user data – which can have serious consequences. Important documents from SharePoint or email boxes should be backed up with a third-party tool. In this case, we recommend Veeam software.